服务承诺
 资金托管
资金托管
 原创保证
原创保证
 实力保障
实力保障
 24小时客服
24小时客服
 使命必达
使命必达
51Due提供Essay,Paper,Report,Assignment等学科作业的代写与辅导,同时涵盖Personal Statement,转学申请等留学文书代写。
 51Due将让你达成学业目标
51Due将让你达成学业目标 51Due将让你达成学业目标
51Due将让你达成学业目标 51Due将让你达成学业目标
51Due将让你达成学业目标 51Due将让你达成学业目标
51Due将让你达成学业目标私人订制你的未来职场 世界名企,高端行业岗位等 在新的起点上实现更高水平的发展
 积累工作经验
积累工作经验 多元化文化交流
多元化文化交流 专业实操技能
专业实操技能 建立人际资源圈
建立人际资源圈Security in multicasting--澳洲Paper代写范文
2016-09-21 来源: 51Due教员组 类别: Paper范文
澳洲Paper代写范文:“Security in multicasting”,这篇论文主要描述的是随着时代的发展和技术的进步,以往所使用的多播也因为效率低下、易受攻击等原因在人们生活中的使用频率在逐渐的降低,为了能够解决多播所存在的问题,我们需要提高安全服务策略,从认证、授权、加密、数据完整四个方面出发,全面提高多播的安全性。
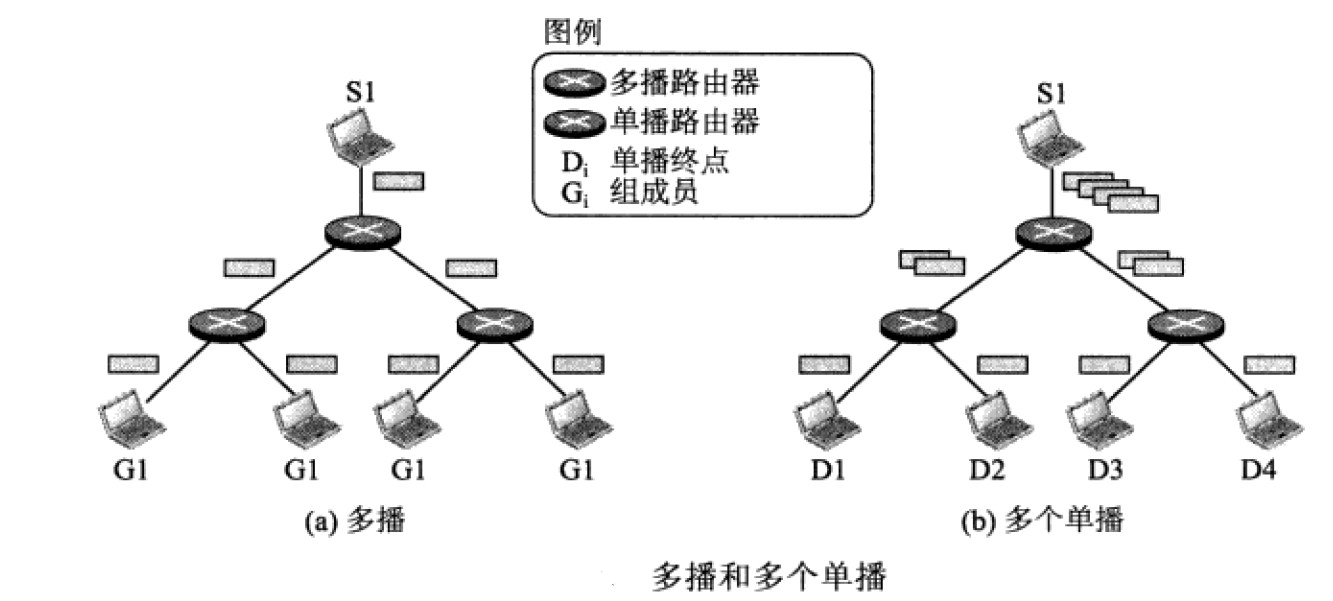
Security in multicasting is one of the main and important issues. Multicast services require more security than the unicast services. In multicasting process more entities participate with each other without any trusted relationship. Threats include the unauthorized creation, alteration, destruction, and illegitimate use of data.The scope of multicast session is broad as compared to unicast session that's why it is much vulnerable to security attacks.
To reduce multicast security issues we can implement many security services. These services can be further categories into four areas such as authentication, authorization, encryption and data integrity as defined .To minimize security issues multicast communication may use all or some of the services to get a required level of security. The services needed for a security level will be defined by a certain policy under the specific requirements and needs of the session.
Authentication service is process of providing assurance of the participating host identity, so they may be allowed to create, send or receive data and to execute specific tasks. With help of authentication only Authorized hosts are permitted to join a secure multicast group.
More over authentication is a vital part in offering control to key material. If cryptographic techniques like as encryption for confidentiality are applied then authentication may offer a method to control access to keys used to secure group communication. For the establishment of session availability and distribution of keys only authorized group members should access those keys. In order to identify the source of multicast traffic, authentication mechanisms may be applied by the traffic source.
This application serves to further define group membership by positively identifying group members along with their data being sourced to the group. Protocols such as the IP Authentication Header (AH) can provide authentication for IP datagrams and may be used for host authentication . Authentication is also an essential part of any key distribution protocol .
To counter various masquerades and replay attacks that may be conducted against a secure multicast session keying material is used because it can identify the source of the key material. By applying authentication pattern to multicast groups data can achieve strong level of integrity.
Integrity services provide assurance that multicast traffic is not changed during transmission. Integrity is not inherent to IP datagram traffic payloads and is usually reserved for transport layer protocols. The lack or weakness of integrity services in IP can lead to spoofing attacks .
Strong integrity mechanisms can be applied indirectly at the network layer with security protocols such as the Encapsulating Security Payload (ESP) and AH . The applications having key management protocols, integrity services are necessary against spoofing attacks.
Confidentiality services are important in creating a private multicast session. Normally encryption is used for establishment of private multicast sessions. With time/-to/-live (TTL) setting we can get a weaker form confidentiality by restricting data distribution of routed session.
On different layers of protocol stack encryption can be applied to end services. At network layer, ESP provides confidentiality services for IP datagrams through encryption. Key management protocols such as the Internet Security Association and Key Management Protocol (ISAKMP) support confidentiality services for key exchanges.
关键管理问题---Issues of key management:
We can accomplish required levels of confidentiality, integrity and authentication for multicast session by use of encryption and digital signatures. By having a robust security mechanism which cannot be easily defeated by cryptanalytic attacks, our concentration is now on key management, key distribution and access control for protecting key material. For this reason, secure multicast session has class D IP address and essential keying material. The encryption mechanism, enforced security policy and key structure dictate size, type and number of keys to guard multicast session.
In order to maintain the security of session access to these keys must restricted. So, strong authentication mechanism should be applied during the registration process before distributing key material to each device. When these personal attributes are bound to a signed digital certificate, the certificate's digital signature and its relationship in a certificate hierarchy may verify the identity of a participant and their assigned permissions.
In a multicast session it may be required to issue a new key or rekey depending on the security policy and traffic flow encrypted under a certain key. A rekey can also be done in case suspected event is detected. Rekey is sometime performed to deny the access to compromised site for future communication, without heavily affecting the other devices.
Depending on the implemented security mechanism, voluntary exit of a device from a session is also included in compromise category. Rekey is required sometimes to prevent the previous device from joining the session without re registration. The need of rekey is dependent upon policy issues as well as practical tradeoffs. Policy of "flat or hierarchical" group trust is efficient in some scenarios greatly decreasing complexity required for dynamic key management.
51due留学教育原创版权郑重声明:原创留学生作业代写范文源自编辑创作,未经官方许可,网站谢绝转载。对于侵权行为,未经同意的情况下,51Due有权追究法律责任。
51due为留学生提供最好的服务,亲们可以进入主页了解和获取更多澳洲paper代写范文 提供美国作业代写以及paper辅导服务,详情可以咨询我们的客服QQ:800020041哟。-xz



